How to Stop Distributed Denial of Service (DDOS): Why not try BCP38?

Mack Coulibaly, CEO, Jighi
I was saddened to see that a Denial of Service (DOS) or a Distributed Denial of Service (DDOS) attack has brought down Internet services for more than 40 Millions users in the East Coast of the United States. DOS attacks are those launched across the Internet to take websites and other services off the air, often utilizing 'bots / Botnet' on infected home and business computers. In fact, we may sometimes be complicit and participating in the attack without our knowledge. The astonishing thing is that DOS attacks are nothing new. They have been around since the early days of the Internet.
Case and point, take for example RFC2827, which is also referred today as BCP38 (Business Current Practice 38):
The Abstract of the RFC2827 reads: “Recent occurrences of various Denial of Service (DoS) attacks which have employed forged source addresses have proven to be a troublesome issue for Internet Service Providers and the Internet community overall. This paper discusses a simple, effective, and straightforward method for using ingress traffic filtering to prohibit DoS attacks which use forged IP addresses to be propagated from 'behind' an Internet Service Provider's (ISP) aggregation point."
Note: BCP38 is RFC2827: Network Ingress Filtering: Defeating Denial of Service Attacks which employ IP Source Address Spoofing.
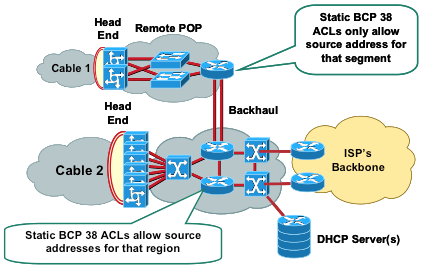
Image from BCP38 page
Paul Ferguson and Daniel Senie wrote the above Abstract in May of the year 2000 as part of the abstract of RFC2827. As an employee at Cisco Systems where Ferguson was also employed at the time, I had reviewed RFC2827 as part of a process to include its features in the Cisco IOS Software. Yes, that was 16 years ago!
Over the past 16 years, cyber criminals have sharpened their tools to a point that today, it is really easy and very low cost to launch a DDOS attacks with impunity; helped by the fact that one can hide behind forged source IP addresses.
Just last year, in February 2015, the Internet Society convened a roundtable bringing together network operators, vendors, leading security experts, and researchers in this area to discuss the problem of source IP address spoofing with a goal to better understand the challenges of addressing it or help solve the problem, and to identify paths to improve the situation going forward. It seems that BCP38 can help make a dent in the arrogance of those who disrupt our lives at will. The logic is that without spoofed IP addresses, there will be no Distributed Denial of Service (DDoS) attacks.
I am not stating that BCP 38, which essentially blocks (or drops) packets from forged source IP addresses from entering the Internet will solve all DOS attacks. In fact, we know that there is a small chance that non-fraudulent packets will also be dropped and that network operators may have to handled those exceptions manually. But those efforts are a small price to pay for our protection.
Some may argue that if it is that easy, why didn't people do it? I ask myself the same question every time there is one of these flamboyant attacks. Maybe some people don't know they can do some thing about it. Maybe they don’t know they should do something about it. Or maybe they just don’t know. That is one of the reasons Jighi is proudly sponsoring the Ivoire Cyber Security Conference on November 9 – 10 in an attempt to educate and build a community of concerned cyber citizen.
For those who think that BCP38 is not be perfect, I say: it gives us a way to stop an attack before it causes systems to go down. It also gives us a way to track weaponized packets to their source; unlike today situation where we are left to speculate. Today’s attack, as reported by CNN simply crippled Amazon, Reddit, Twitter, Netflix and others.
Whatever the reasons for our lack of actions, the current Cyber Space is not sustainable.Attackers have more and more sophisticated tools and we are unable to come together to tackle this phenomenon. I say, let's give a chance to BCP38. Let's eliminate the easy things with seemingly easy solutions: DOS attacks, and their even nastier cousins Distributed Denial Of Service attacks are easy to do and hard to deal with because of the forged IP addresses. That situation is made worse because the attack cannot be quickly stopped. Why? Because forged source IP addresses make it impossible to determine where the attack is actually coming from.
Subscribe to Industry Era
News
This Apple Watch Case Could Kill All of Those Wannabe AI Devices
Google defends AI search results after they told us to put glue on pizza
Google scales back AI search answers after it told users to eat glue
FAA won't approve increased 737 Max production in near future
Thursday was a sour day for the US economy — with an important silver lining
OPEC+ working on complex production cut deal for 2024-2025, sources say
Stock futures inch lower as investors review earnings, brace for inflation report: Live updates
Salesforce Shares Plunge by Most Since 2008 After Weak Outlook
Jeep’s Wagoneer S Trailhawk concept teases a fully electric off-roader
Gap’s stock jumps 23% as the retailer swings to profit and raises guidance
Medline recalls 1.5 million bed rails linked to deaths of 2 women
Oil falls as Fed policymakers look to maintain rate cuts, gasoline stocks rise